
Quantum Computing’s Impact on Encryption: US Data Security
The advent of quantum computing poses an imminent threat to current encryption standards, demanding urgent preparation for US data security over the next five years. Proactive strategies are crucial to safeguard sensitive information.

Act Now: Time-Sensitive Digital Privacy Settings Before March 2025
Before March 2025, proactive adjustment of three time-sensitive digital privacy settings is paramount to protect personal information and enhance online security against evolving threats.

Cyber Risk: US Employee Training Mandates by June 2025
New US mandates for employee cyber security training are expected by June 2025, aiming to mitigate significant cyber risks posed by human error. This article explores these crucial updates, their implications for businesses, and how to prepare your workforce for enhanced data protection.

Threat Intelligence Platforms: 2025 Comparison for US Organisations
This article offers a comprehensive 2025 comparison of leading threat intelligence platforms, specifically tailored for US organisations to enhance their detection capabilities against evolving cyber threats.
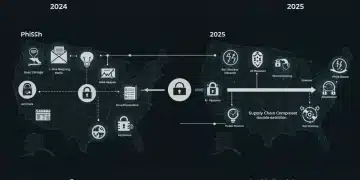
Ransomware Tactics: 2024 vs. 2025 US Threat Landscape Analysis
The US ransomware landscape is rapidly evolving, with 2025 expected to see more sophisticated attacks than 2024, driven by AI, supply chain exploitation, and nation-state involvement. Proactive defence is paramount.

Top 4 Privacy Browsers 2025: US Data Protection Comparison
For US users prioritising digital anonymity, selecting a robust privacy-focused browser is crucial in 2025, offering essential data protection against pervasive tracking and safeguarding personal information.





