AI Cyber Threats: US Critical Infrastructure Forecast
A 3-month forecast reveals that emerging AI-powered cyber threats: a 3-month forecast for US critical infrastructure (time-sensitive) poses an immediate and evolving risk, necessitating advanced defensive strategies to protect essential national systems from sophisticated digital attacks.
The digital landscape is in a constant state of flux, with new challenges emerging at an unprecedented pace. Among these, the rise of emerging AI-powered cyber threats: a 3-month forecast for US critical infrastructure (time-sensitive) stands out as a particularly pressing concern. This article delves into the immediate future, exploring how artificial intelligence is being weaponised by malicious actors and what this means for the backbone of the United States.
The Escalating Threat Landscape of AI-Powered Attacks
The integration of artificial intelligence into cybersecurity has been a double-edged sword. While AI offers powerful tools for defence, it simultaneously provides adversaries with advanced capabilities to launch more sophisticated, evasive, and scalable attacks. The next three months are expected to witness a significant escalation in the use of AI by threat actors targeting the critical infrastructure of the US.
This surge is driven by several factors, including the increasing accessibility of AI tools, the growing complexity of digital ecosystems, and the continuous search for new vulnerabilities. Understanding these dynamics is paramount for developing effective countermeasures and safeguarding national assets.
Automated Reconnaissance and Exploitation
AI algorithms are now being employed to automate and accelerate the reconnaissance phase of cyberattacks. This involves scanning vast networks for vulnerabilities, identifying misconfigurations, and mapping out potential entry points with unparalleled efficiency. The speed and accuracy of AI-driven reconnaissance significantly reduce the time required for attackers to prepare their operations.
- Target Identification: AI quickly sifts through public and dark web data to identify high-value targets within critical infrastructure sectors.
- Vulnerability Mapping: Machine learning models analyse system configurations and patch levels to pinpoint exploitable weaknesses.
- Behavioural Analysis: AI can mimic legitimate network traffic to bypass traditional intrusion detection systems, making it harder to detect initial breaches.
Once vulnerabilities are identified, AI can also assist in the automated generation of exploits. This means that custom malware can be developed and deployed faster, tailored specifically to the target’s environment, thereby increasing the success rate of attacks and reducing the window of opportunity for defenders.
Deepfake and Phishing Campaigns
The use of AI in social engineering attacks, particularly deepfakes and advanced phishing, is set to become more prevalent and convincing. Deepfake technology can generate highly realistic audio and video impersonations, making it incredibly difficult for individuals to discern genuine communications from malicious ones.
These sophisticated scams can be used to trick employees of critical infrastructure entities into revealing sensitive information, granting unauthorised access, or executing fraudulent transactions. The human element often remains the weakest link in cybersecurity, and AI is making this vulnerability even more pronounced.
The rapid evolution of generative AI tools means that phishing emails and messages can be crafted with perfect grammar, contextual relevance, and personalised content, bypassing traditional spam filters and human scrutiny more effectively than ever before. This significantly increases the likelihood of successful credential harvesting or malware delivery.
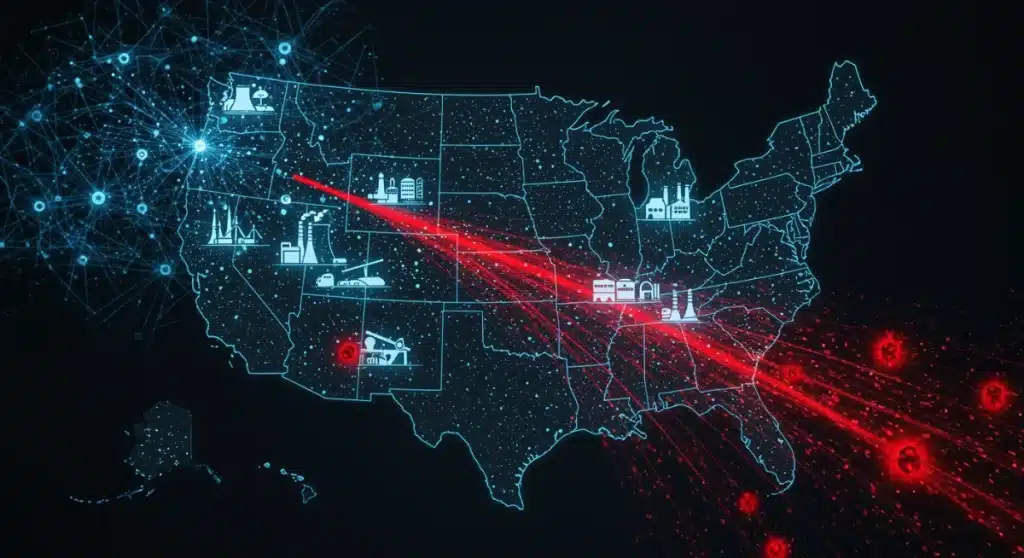
Key Critical Infrastructure Sectors at Risk
The US critical infrastructure encompasses a wide array of sectors vital for national security, economic stability, and public health. Each sector presents unique vulnerabilities and potential targets for AI-powered cyber adversaries. The next three months will likely see increased attention on specific areas due to their interconnectedness and potential for widespread disruption.
Understanding which sectors are most susceptible and why is crucial for prioritising defensive efforts and allocating resources effectively. The ripple effects of an attack on one sector can quickly cascade to others, amplifying the overall impact.
Energy Sector Vulnerabilities
The energy sector, including power grids, oil and gas pipelines, and nuclear facilities, remains a prime target due to its foundational role in society. AI-powered attacks could aim to disrupt power supply, manipulate energy markets, or even cause physical damage to infrastructure. The interconnected nature of smart grids offers numerous entry points.
- Operational Technology (OT) Compromise: AI can identify and exploit vulnerabilities in industrial control systems (ICS) and supervisory control and data acquisition (SCADA) systems.
- Supply Chain Attacks: Attacks on third-party vendors providing software or hardware to energy companies can create backdoor access.
- Distributed Denial of Service (DDoS): AI-orchestrated botnets can launch massive DDoS attacks to overwhelm energy sector networks, causing outages.
The potential for widespread blackouts or fuel shortages makes this sector exceptionally attractive to nation-state actors and sophisticated cybercriminals seeking to cause significant economic and social disruption. The increasing digitisation of energy management systems further broadens the attack surface.
Water and Wastewater Systems
Water and wastewater systems are equally critical, providing essential services for public health and safety. These systems often operate with legacy equipment and may have fewer cybersecurity resources compared to other sectors, making them particularly vulnerable to AI-powered threats. Compromising these systems could lead to contamination or service disruption.
Attackers could use AI to gain control of water flow, chemical treatment processes, or monitoring systems, potentially leading to widespread public health crises. The consequences of such an attack could be devastating, impacting millions of citizens and requiring extensive recovery efforts.
Healthcare and Public Health
The healthcare sector, already grappling with ransomware and data breaches, faces heightened risks from AI-powered threats. Attacks could target patient records, medical devices, or hospital operational systems, leading to severe disruptions in patient care, data theft, and even loss of life. The sensitive nature of health data makes it a lucrative target for extortion.
AI can accelerate the exfiltration of massive volumes of patient data, making it easier for attackers to identify and exploit vulnerabilities in electronic health record (EHR) systems. Furthermore, AI could be used to manipulate medical device software, posing direct threats to patient safety.
Advanced AI-Driven Attack Vectors to Watch
The sophistication of AI-powered cyberattacks is continuously evolving, introducing new and complex attack vectors. Over the next three months, critical infrastructure defenders must be vigilant against these emerging methods, which leverage AI to bypass traditional security measures and exploit novel weaknesses.
These advanced techniques often combine multiple AI capabilities, making them highly adaptive and difficult to detect. Proactive intelligence gathering and predictive analysis are becoming indispensable components of a robust defence strategy.
Reinforcement Learning for Evasion
Attackers are beginning to employ reinforcement learning (RL) algorithms to train malware to evade detection. RL agents can learn from their interactions with defensive systems, adapting their tactics, techniques, and procedures (TTPs) in real-time to bypass firewalls, intrusion detection systems, and antivirus software. This creates highly dynamic and polymorphic threats.
The malware can continuously modify its code, network behaviour, and execution patterns based on feedback from the target environment. This adaptive capability makes it incredibly challenging for signature-based and even some behavioural-based detection systems to keep pace.
Autonomous Attack Agents
The concept of autonomous attack agents, powered by AI, is moving from theoretical discussion to practical implementation. These agents can operate independently, making decisions about targets, attack methods, and evasion strategies without constant human intervention. This significantly increases the speed and scale of cyber campaigns.
- Self-Propagating Malware: AI agents can develop and deploy self-propagating malware that identifies and exploits new vulnerabilities across networks autonomously.
- Adaptive Persistence: They can learn to maintain persistence within compromised systems, adapting to system changes and defender actions to avoid removal.
- Target Prioritisation: Autonomous agents can dynamically prioritise targets based on their perceived value and vulnerability, optimising attack effectiveness.
The ability of these agents to operate with minimal human oversight means that attacks can be launched and sustained around the clock, overwhelming human defenders and traditional incident response protocols. The speed at which these agents can compromise systems necessitates automated defensive responses.
AI in Supply Chain Attacks
Supply chain attacks are becoming increasingly complex, with AI playing a role in identifying weak links and orchestrating multi-stage compromises. Attackers can use AI to analyse the entire supply chain of a critical infrastructure entity, pinpointing vulnerable third-party vendors or software components.
Once a weak link is identified, AI can assist in crafting highly targeted attacks that compromise the vendor, injecting malicious code or backdoors into legitimate software updates or hardware before they reach the ultimate target. This method allows attackers to bypass the direct defences of the critical infrastructure entity by exploiting trusted relationships.
Mitigation Strategies and Proactive Defence
Given the rapidly evolving nature of AI-powered cyber threats, a proactive and multi-layered defence strategy is essential for protecting US critical infrastructure. This involves a combination of technological advancements, policy enhancements, and human expertise. The next three months are a critical window for implementing and strengthening these measures.
Organisations must move beyond reactive defence and adopt a forward-thinking approach that anticipates future threats. Collaboration between government agencies, private industry, and cybersecurity experts is paramount to building a resilient national defence.
Enhanced Threat Intelligence and Sharing
Real-time threat intelligence sharing among critical infrastructure sectors, government agencies, and cybersecurity firms is more important than ever. AI can be leveraged to analyse vast quantities of threat data, identify emerging patterns, and predict potential attack vectors before they materialise. This proactive intelligence allows for timely defensive adjustments.
Establishing robust information sharing and analysis centres (ISACs) and encouraging participation are vital steps. These platforms facilitate the rapid dissemination of indicators of compromise (IoCs), attacker TTPs, and best practices, enabling collective defence against sophisticated AI-powered threats.
AI-Powered Defensive Systems
To combat AI-powered attacks, critical infrastructure must deploy equally advanced AI-powered defensive systems. These systems can detect anomalies, identify malicious behaviour, and respond to threats at machine speed, often outperforming human analysts in the initial stages of an attack.
- Behavioural Analytics: AI-driven systems can establish baseline normal behaviour and flag deviations that indicate compromise or attack attempts.
- Automated Incident Response: AI can automate parts of the incident response process, such as isolating compromised systems or deploying patches, reducing reaction time.
- Predictive Security: Machine learning models can predict future attack trends based on historical data and current threat intelligence, allowing for proactive security posture adjustments.
Investing in technologies such as AI-driven extended detection and response (XDR) platforms and security orchestration, automation, and response (SOAR) solutions will be crucial for maintaining a competitive edge against AI-enabled adversaries. These systems can process and correlate data from various sources, providing a holistic view of the threat landscape.

Policy and Regulatory Frameworks
The rapid advancement of AI-powered cyber threats necessitates a corresponding evolution in policy and regulatory frameworks. Governments must work collaboratively with industry to establish clear guidelines, standards, and incentives for improving cybersecurity posture across critical infrastructure sectors. This includes addressing the unique challenges posed by AI.
Effective policy can drive investment in cybersecurity, mandate minimum security standards, and foster a culture of resilience. Without a robust regulatory environment, individual entities may struggle to keep pace with the escalating threat landscape.
Mandatory Cybersecurity Standards
The implementation of mandatory cybersecurity standards tailored to the unique risks of AI-powered threats is essential. These standards should cover areas such as secure AI development, responsible AI deployment, and robust incident response protocols specific to AI-enabled attacks. Regular audits and compliance checks would ensure adherence.
Furthermore, these standards should encourage the adoption of zero-trust architectures and continuous monitoring, recognising that traditional perimeter-based defences are insufficient against adaptive AI threats. The focus should be on protecting data and systems regardless of their location.
International Collaboration and Treaties
Cyber threats transcend national borders, making international collaboration indispensable. Engaging with allies and international organisations to establish norms for responsible AI use, share threat intelligence, and coordinate defensive efforts is critical. Treaties and agreements can help deter nation-state actors from weaponising AI against critical infrastructure.
Joint exercises and information-sharing initiatives can enhance collective defence capabilities, ensuring that a coordinated response can be mounted against large-scale, AI-orchestrated cyberattacks that target multiple nations simultaneously. Diplomacy and technical collaboration must go hand in hand.
Developing a Resilient Workforce
Technology alone cannot solve the complex challenge of AI-powered cyber threats. A highly skilled and resilient cybersecurity workforce is the ultimate defence. Investing in education, training, and talent development programmes is crucial to ensure that critical infrastructure entities have the human expertise required to manage, detect, and respond to advanced threats.
The demand for cybersecurity professionals with AI expertise far outstrips supply, creating a significant talent gap. Addressing this gap requires a concerted effort from government, academia, and industry to cultivate the next generation of cyber defenders.
Specialised AI Cybersecurity Training
Cybersecurity professionals within critical infrastructure must receive specialised training in AI-driven attack techniques and defensive measures. This includes understanding machine learning fundamentals, AI-specific vulnerabilities, and how to operate AI-powered security tools effectively. Continuous learning programmes are essential to keep skills current.
- Threat Hunting: Training in AI-assisted threat hunting to proactively search for hidden threats within complex networks.
- AI Model Security: Education on securing AI models themselves from adversarial attacks, ensuring their integrity and reliability.
- Incident Response: Developing protocols for responding to incidents involving AI-powered malware and autonomous agents.
Simulations and tabletop exercises that mimic AI-powered attack scenarios can provide invaluable hands-on experience, preparing teams for real-world incidents. These exercises help identify weaknesses in existing response plans and improve coordination.
Cross-Sector Knowledge Transfer
Facilitating knowledge transfer and collaboration between cybersecurity teams across different critical infrastructure sectors can enhance overall resilience. Sharing best practices, lessons learned from incidents, and insights into AI-powered threats can create a collective intelligence network that benefits all participants.
Mentorship programmes, industry conferences, and shared research initiatives can foster an environment of continuous learning and adaptation. Building a strong community of practice among cybersecurity professionals is a long-term investment in national security.
| Key Threat | Brief Description |
|---|---|
| Automated Exploitation | AI swiftly identifies and exploits system vulnerabilities, accelerating attack timelines and reducing defender response windows. |
| Deepfake Social Engineering | Highly realistic AI-generated audio/video impersonations and phishing campaigns trick personnel into compromising systems. |
| Reinforcement Learning Evasion | Malware adapts in real-time using AI to bypass detection, making traditional security measures less effective and harder to trace. |
| Autonomous Attack Agents | AI agents operate independently to select targets, execute attacks, and evade detection without constant human oversight, increasing scale and speed. |
Frequently Asked Questions About AI Cyber Threats
AI-powered threats are dangerous due to their speed, scalability, and adaptability. They can automate reconnaissance, generate sophisticated exploits, and learn to evade detection in real-time, making them far more effective and harder to counter than traditional cyberattacks against vital national systems.
In the coming three months, the energy, water, and healthcare sectors are expected to face heightened risks. Their interconnectedness, reliance on operational technology, and potential for widespread disruption make them prime targets for AI-driven cyber adversaries seeking maximum impact.
Defending against AI-driven social engineering requires robust employee training, multi-factor authentication, and verification protocols. Employees must be educated to recognise deepfake indicators and verify unusual requests through alternative, trusted communication channels before acting.
AI-powered defensive systems are crucial for detecting anomalies, identifying malicious behaviour, and responding to threats at machine speed. They can analyse vast data, automate incident response, and offer predictive security insights, providing a vital edge against sophisticated AI-enabled attacks.
Effective policy requires mandatory cybersecurity standards for AI development and deployment, alongside robust incident response protocols. International collaboration, threat intelligence sharing, and treaties are also essential to establish norms and coordinate global defence efforts against AI-powered cyber warfare.
Conclusion
The forecast for the next three months indicates a significant and urgent challenge for US critical infrastructure, driven by the escalating sophistication of AI-powered cyber threats. From automated exploitation and deepfake social engineering to autonomous attack agents, the vectors for compromise are becoming more evasive and impactful. Protecting these vital systems demands a multi-faceted approach encompassing advanced AI-powered defensive technologies, enhanced threat intelligence sharing, robust policy frameworks, and a highly skilled cybersecurity workforce. Proactive measures, continuous adaptation, and collaborative efforts across all sectors are not merely advisable but absolutely essential to safeguard national security and public well-being in this rapidly evolving digital battleground.