Ransomware Attacks US Q4 2024: Small Business Protection

Ransomware attacks in the US surged by 20% in Q4 2024, critically impacting small businesses; implementing robust cybersecurity measures and proactive defence strategies is paramount for protection.
The alarming rise in ransomware attacks in the US surged by 20% in Q4 2024: practical solutions for small business protection is no longer a distant threat but an immediate crisis demanding urgent attention. Small businesses, often seen as easier targets due to limited resources, are increasingly falling victim to sophisticated cybercriminals.
Understanding the Escalation of Ransomware Threats
The digital landscape continually evolves, bringing with it new opportunities but also heightened risks. The recent 20% surge in ransomware attacks against US businesses in the final quarter of 2024 paints a stark picture of the growing cyber threat, particularly for small and medium-sized enterprises (SMEs). This escalation isn’t merely a statistic; it represents real businesses facing operational paralysis, significant financial losses, and reputational damage.
Several factors contribute to this alarming trend. Cybercriminals are becoming more sophisticated, employing advanced social engineering tactics, zero-day exploits, and highly evasive malware. The increasing reliance on digital infrastructure, cloud services, and remote work, while beneficial for productivity, also expands the attack surface, creating more entry points for malicious actors.
The Evolving Nature of Ransomware
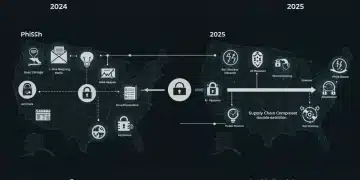
Ransomware has moved beyond simple encryption. Modern attacks often include data exfiltration, where sensitive information is stolen before encryption, leading to ‘double extortion’ threats. If a victim refuses to pay the ransom for decryption, their data is then threatened with public release, increasing the pressure to comply.
- Targeted Attacks: Cybercriminals are increasingly targeting specific industries or businesses with tailored phishing campaigns.
- Ransomware-as-a-Service (RaaS): This model lowers the barrier to entry for aspiring attackers, making sophisticated tools accessible to a wider range of malicious actors.
- Supply Chain Compromises: Attacking a small business that is part of a larger supply chain can provide a backdoor into bigger organisations, making SMEs indirect targets for high-value hacks.
The financial and operational impact of a ransomware attack can be catastrophic for a small business. Beyond the immediate ransom payment, there are costs associated with system recovery, potential legal fees, regulatory fines for data breaches, and the immense loss of customer trust. Understanding these multifaceted risks is the first step towards building a resilient defence.
Proactive Cybersecurity Foundations for Small Businesses
Building a robust cybersecurity posture doesn’t require an infinite budget, but it does demand a strategic and consistent approach. For small businesses, establishing strong foundational security practices is paramount to mitigating the risk of ransomware attacks. These foundations act as the first line of defence, making it significantly harder for cybercriminals to gain a foothold.
It begins with a comprehensive understanding of your digital assets and potential vulnerabilities. Many small businesses operate under the misconception that they are too insignificant to be targeted, a notion that sophisticated attackers readily exploit. Instead, every business, regardless of size, must assume it is a potential target and implement proportionate safeguards.
Essential Security Measures
Implementing a layered security approach is crucial. No single solution offers complete protection; rather, it’s the combination of various tools and practices that creates a strong defence. This includes both technological safeguards and human-centric policies.
- Regular Data Backups: Implement a robust backup strategy, including offsite and offline backups, to ensure data can be restored even if primary systems are compromised.
- Endpoint Protection: Deploy next-generation antivirus and anti-malware solutions on all devices, including laptops, desktops, and mobile phones.
- Firewall Configuration: Properly configure firewalls to monitor and control incoming and outgoing network traffic, blocking unauthorised access.
- Patch Management: Keep all operating systems, applications, and firmware updated to patch known vulnerabilities that attackers frequently exploit.
A proactive stance also involves continuous monitoring and evaluation of security systems. Cyber threats are dynamic, and security measures must adapt accordingly. Regular security audits and vulnerability assessments can help identify weaknesses before they are exploited, allowing businesses to address them promptly and effectively. This continuous improvement cycle is key to maintaining a strong defensive posture against evolving ransomware threats.
Employee Training: The Human Firewall
Even the most advanced technological safeguards can be rendered ineffective if employees are not adequately trained. The human element often represents the weakest link in a cybersecurity chain, particularly when it comes to social engineering tactics like phishing, which are frequently used to deploy ransomware. Empowering employees with knowledge and awareness transforms them into a critical line of defence – a ‘human firewall’.
Many ransomware attacks begin with a deceptive email or a malicious link clicked by an unsuspecting employee. These attacks exploit human curiosity, urgency, or fear to trick individuals into compromising their own systems. Therefore, investing in regular and engaging cybersecurity training is not an option but a necessity for small businesses.
Key Training Areas
Effective training programmes should cover a range of topics, focusing on practical recognition and response strategies. It’s not enough to simply tell employees what not to do; they need to understand why certain actions are risky and how to identify suspicious activity.
- Phishing Awareness: Teach employees to recognise phishing emails, suspicious links, and malicious attachments. Conduct simulated phishing exercises to test their vigilance.
- Strong Password Practices: Emphasise the importance of unique, complex passwords and the use of multi-factor authentication (MFA) wherever possible.
- Data Handling Protocols: Educate staff on the secure handling of sensitive data, both internally and when sharing information externally.
- Incident Reporting: Establish clear procedures for reporting suspected security incidents, ensuring employees know who to contact and what information to provide.
Training should not be a one-off event but an ongoing process. Regular refreshers, updated content reflecting current threats, and interactive sessions can help maintain employee awareness and reinforce best practices. A culture of security, where every employee feels responsible for protecting the business’s digital assets, is invaluable in the fight against ransomware.
Implementing Multi-Factor Authentication (MFA) and Strong Passwords
One of the simplest yet most effective measures a small business can implement to significantly reduce the risk of ransomware attacks is the widespread adoption of multi-factor authentication (MFA) and the enforcement of strong password policies. While passwords alone can be compromised through various means, MFA adds an essential layer of security, making it much harder for unauthorised users to gain access even if they manage to obtain credentials.
MFA requires users to provide two or more verification factors to gain access to an account. This typically involves something the user knows (like a password), something the user has (like a smartphone or a hardware token), and/or something the user is (like a fingerprint or facial scan). This multi-layered approach dramatically reduces the success rate of credential theft attacks, which are often precursors to ransomware deployment.
Best Practices for MFA and Passwords
Implementing MFA across all critical systems and user accounts should be a top priority. This includes email, cloud services, network access, and any applications containing sensitive data. Alongside MFA, strict password policies must be enforced to ensure initial access points are as secure as possible.
- Mandate MFA: Make MFA compulsory for all employee accounts, especially for remote access, administrative privileges, and critical business applications.
- Complex Passwords: Enforce policies that require strong, unique passwords that are at least 12-16 characters long, combining upper and lowercase letters, numbers, and symbols.
- Password Managers: Encourage or provide employees with a reputable password manager to securely store and generate complex passwords, reducing the burden of remembering multiple unique credentials.
- Regular Password Changes: While MFA reduces the immediate need for frequent password changes, periodic updates can still add an extra layer of security.
The combination of robust password practices and universal MFA implementation creates a formidable barrier against many common cyber attack vectors. For small businesses, these measures represent a cost-effective way to elevate their security posture significantly without requiring extensive technical expertise or expensive hardware. It’s a foundational step towards building resilience against the persistent threat of ransomware.
Incident Response and Recovery Planning
Even with the most rigorous preventative measures, no business is entirely immune to cyber attacks. Therefore, having a well-defined incident response and recovery plan is not merely good practice but an absolute necessity for small businesses. A clear plan dictates how your organisation will react to, contain, and recover from a ransomware attack, minimising downtime and financial impact.
Many small businesses overlook this critical aspect, believing that an attack will never happen to them or that they can figure it out on the fly. This reactive approach often leads to panic, delayed responses, and significantly higher recovery costs. A proactive plan ensures that everyone knows their role and responsibilities when a breach occurs, leading to a more organised and efficient recovery.
Elements of an Effective Plan
An incident response plan should be comprehensive yet flexible, outlining steps from initial detection to post-incident review. It should be regularly reviewed and updated, and employees should be familiar with its key components.
- Detection and Analysis: Establish procedures for identifying a suspected ransomware attack, including monitoring system logs and user behaviour anomalies.
- Containment: Outline steps to isolate affected systems and networks to prevent the ransomware from spreading further. This might involve disconnecting compromised devices or segmenting networks.
- Eradication: Detail the process for removing the ransomware, restoring systems from clean backups, and patching vulnerabilities that allowed the attack.
- Recovery: Define procedures for bringing affected systems back online, verifying their integrity, and monitoring for any lingering threats.
- Post-Incident Review: Conduct a thorough analysis after an attack to understand what happened, why it happened, and what can be done to prevent future occurrences.

Regular testing of the incident response plan through tabletop exercises or simulated attacks is vital. This helps identify weaknesses in the plan and familiarises staff with the protocols, ensuring a smoother and more effective response should a real incident occur. For a small business, a well-executed recovery plan can be the difference between a minor setback and business-ending catastrophe.
Cyber Insurance and Regulatory Compliance
While preventative measures and response plans are crucial, small businesses should also consider the financial protection offered by cyber insurance. Furthermore, understanding and adhering to relevant data protection regulations is not just about avoiding penalties; it’s about building trust and demonstrating a commitment to data security. Both aspects form an integral part of a comprehensive cybersecurity strategy.
Cyber insurance is specifically designed to help businesses recover from cyber incidents, covering costs such as data restoration, business interruption, legal fees, and even ransom payments (though paying ransoms is generally discouraged by law enforcement). For small businesses, where financial reserves may be limited, this can provide a vital safety net against the potentially crippling costs of a ransomware attack.
Navigating Regulations and Insurance
The regulatory landscape regarding data privacy and security is complex and constantly evolving. Small businesses must be aware of their obligations, especially if they handle sensitive customer data or operate in regulated industries. Compliance not only reduces legal risks but also often aligns with best security practices.
- Evaluate Cyber Insurance Needs: Work with an insurance broker to assess your business’s specific risks and determine appropriate coverage levels. Understand what is and isn’t covered by policies.
- Understand Data Protection Laws: Familiarise yourself with regulations like GDPR (if dealing with EU citizens), CCPA (for California residents), and industry-specific mandates (e.g., HIPAA for healthcare).
- Implement Compliance Frameworks: Adopt recognised cybersecurity frameworks (e.g., NIST Cybersecurity Framework, ISO 27001) that can guide your security efforts and demonstrate due diligence.
- Regular Audits: Conduct periodic internal or external audits to ensure ongoing compliance with regulatory requirements and internal security policies.
Investing in cyber insurance and maintaining regulatory compliance are not alternatives to strong security practices, but rather essential complements. They provide financial protection and a legal framework that supports a business’s overall resilience against cyber threats, offering peace of mind in an increasingly risky digital environment.
Future-Proofing Your Small Business Against Ransomware
The landscape of cyber threats, particularly ransomware, is dynamic and constantly evolving. For small businesses, merely reacting to current threats is insufficient; a forward-thinking approach is necessary to future-proof their operations against emerging ransomware variants and attack methodologies. This involves staying informed, embracing adaptive security tools, and fostering a culture of continuous improvement in cybersecurity practices.
Anticipating future threats means understanding the trends in cybercrime and the technological advancements that might be exploited. This includes the increasing use of artificial intelligence in orchestrating attacks, the targeting of IoT devices, and the exploitation of vulnerabilities in new software and cloud architectures. Small businesses must cultivate a mindset of proactive adaptation rather than passive defence.
Strategies for Long-Term Resilience
Building long-term resilience against ransomware requires a commitment to ongoing education, technology upgrades, and strategic partnerships. It’s about creating a security ecosystem that can evolve as quickly as the threats it faces.
- Threat Intelligence: Stay updated on the latest ransomware trends, attack techniques, and vulnerabilities through reputable cybersecurity news sources and industry reports.
- AI-Powered Security Solutions: Explore and implement security tools that leverage AI and machine learning for advanced threat detection and response, which can identify novel attack patterns.
- Cloud Security Best Practices: For businesses utilising cloud services, ensure robust cloud security configurations, including identity and access management, data encryption, and regular security audits of cloud environments.
- Engage Cybersecurity Professionals: Consider partnering with managed security service providers (MSSPs) or cybersecurity consultants who can offer expert guidance, monitoring, and incident response capabilities, especially if in-house resources are limited.
Future-proofing also involves regular review and updating of all cybersecurity policies and procedures. As your business grows and adopts new technologies, your security framework must expand and adapt to cover these new areas. This continuous vigilance ensures that your small business remains protected against the ever-present and evolving threat of ransomware, safeguarding its continuity and reputation for years to come.
| Key Protection Area | Brief Description |
|---|---|
| Data Backup Strategy | Implement offsite and offline backups to ensure data restorability post-attack. |
| Employee Training | Educate staff on phishing, strong passwords, and incident reporting to create a ‘human firewall’. |
| MFA Implementation | Mandate Multi-Factor Authentication across all critical systems to secure access points. |
| Incident Response Plan | Develop and test a clear plan for detection, containment, eradication, and recovery from attacks. |
Frequently Asked Questions About Ransomware Protection
Ransomware is malicious software that encrypts data, demanding a ransom for its release. Small businesses are targeted due to perceived weaker security postures and limited resources, making them attractive, easier targets for cybercriminals seeking quick profits or access to larger supply chains.
Data backups should be performed regularly, ideally daily or even more frequently for critical data. The frequency depends on how often your data changes and your tolerance for data loss. Ensure backups are stored offsite and are regularly tested for restorability.
Yes, cyber insurance is highly recommended. It provides financial protection against the significant costs associated with cyber attacks, including data recovery, legal fees, business interruption, and potential regulatory fines. It acts as a critical safety net for small businesses.
Effective training should cover phishing awareness, strong password creation and management (including MFA use), secure data handling protocols, and clear procedures for reporting suspicious activities. Regular, engaging sessions are key to building a strong ‘human firewall’.
Yes, recovery without paying the ransom is often possible and recommended, primarily through robust, tested data backups. Paying the ransom does not guarantee data recovery and can fund further criminal activity. A strong incident response and recovery plan is essential for this approach.
Conclusion
The significant surge in ransomware attacks against US small businesses in Q4 2024 serves as a critical wake-up call. While the threat is formidable, effective protection is achievable through a combination of proactive cybersecurity measures, continuous employee education, robust incident response planning, and strategic financial safeguards like cyber insurance. By implementing these practical solutions, small businesses can build resilience, safeguard their operations, and navigate the complex digital landscape with greater confidence, turning a potential catastrophe into a manageable challenge.