CISA Updates Zero Trust Architecture Guidance: Enhancing US Cybersecurity

US Cybersecurity and Infrastructure Security Agency (CISA) has released updated guidance on Zero Trust Architecture, providing enhanced strategies and recommendations for federal agencies to bolster their cybersecurity defenses against evolving threats and modernize their infrastructure.
The **US Cybersecurity and Infrastructure Security Agency (CISA) has released updated guidance on Zero Trust Architecture**, marking a significant step in the ongoing efforts to strengthen the cybersecurity posture of federal agencies and critical infrastructure in the United States. This updated guidance provides a more comprehensive and practical framework for implementing Zero Trust principles, which are crucial in today’s complex and rapidly evolving threat landscape.
What is the Updated CISA Zero Trust Architecture Guidance?
The updated CISA Zero Trust Architecture guidance serves as a roadmap for federal agencies to adopt a more proactive and resilient security model. It emphasizes verifying every user and device before granting access to resources, regardless of their location or network.
This updated guidance builds upon previous versions by incorporating lessons learned from real-world implementations and addressing emerging threats. It aims to provide a clearer and more actionable framework for agencies to follow.
Key Principles of Zero Trust Architecture
Zero Trust Architecture is founded on several core principles that challenge traditional security models. These principles are essential for understanding and implementing Zero Trust effectively.
- Verify Explicitly: Always authenticate and authorize users and devices based on all available data points.
- Least Privilege Access: Grant users only the minimum level of access required to perform their duties.
- Assume Breach: Operate under the assumption that a breach has already occurred, and continuously monitor and validate access.
- Microsegmentation: Divide networks into smaller, isolated segments to limit the impact of a potential breach.
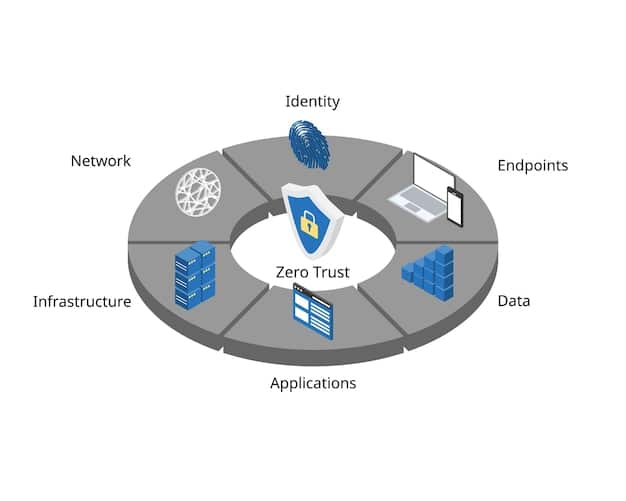
By adhering to these principles, agencies can significantly reduce their attack surface and improve their ability to detect and respond to cyber threats.
In summary, the updated CISA guidance is a critical resource for federal agencies looking to enhance their cybersecurity defenses by adopting a Zero Trust approach. It provides a practical and actionable framework for implementing these principles in a real-world setting.
Why is Zero Trust Architecture Important?
Zero Trust Architecture has become increasingly important in recent years due to the growing sophistication and frequency of cyber attacks. Traditional security models, which rely on perimeter-based defenses, are no longer sufficient to protect against modern threats.
With the rise of remote work and cloud computing, the traditional network perimeter has become increasingly blurred, making it more difficult to secure resources. Zero Trust addresses this challenge by shifting the focus from network location to user and device identity.
Evolving Threat Landscape
The threat landscape is constantly evolving, with attackers using increasingly sophisticated techniques to bypass traditional security measures. Zero Trust helps organizations stay ahead of these threats by continuously monitoring and validating access.
- Ransomware Attacks: Zero Trust can help prevent the spread of ransomware by limiting the access of compromised accounts.
- Insider Threats: By verifying every user and device, Zero Trust can mitigate the risk of insider threats.
- Supply Chain Attacks: Zero Trust can help secure the supply chain by validating the identity of third-party vendors and their devices.
By implementing Zero Trust, organizations can significantly reduce their risk of falling victim to these types of attacks.
In conclusion, Zero Trust Architecture is crucial for organizations looking to protect themselves against modern cyber threats. It provides a more robust and resilient security model that can adapt to the evolving threat landscape.
Key Updates in CISA’s Zero Trust Guidance
The updated CISA Zero Trust Architecture guidance includes several key updates that reflect the latest best practices and lessons learned from real-world implementations. These updates are designed to provide agencies with a more practical and actionable framework for adopting Zero Trust.
One of the most significant updates is the emphasis on automation and orchestration. The guidance highlights the importance of using automation tools to streamline the implementation and management of Zero Trust policies.
Focus on Automation and Orchestration
Automation and orchestration are essential for scaling Zero Trust across large and complex organizations. By automating key processes, agencies can reduce the burden on security teams and improve their overall efficiency.
The updated guidance also provides more detailed guidance on how to integrate Zero Trust with existing security infrastructure. This includes guidance on integrating Zero Trust with identity management systems, security information and event management (SIEM) systems, and other security tools.
In summary, the key updates in CISA’s Zero Trust Architecture guidance reflect the latest best practices and lessons learned from real-world implementations. These updates are designed to provide agencies with a more practical and actionable framework for adopting Zero Trust.
Implementing Zero Trust Architecture: A Step-by-Step Approach
Implementing Zero Trust Architecture is a complex process that requires careful planning and execution. However, by following a step-by-step approach, organizations can successfully adopt Zero Trust and improve their overall security posture.
The first step is to assess the organization’s current security posture. This involves identifying the organization’s assets, vulnerabilities, and threats. It also involves assessing the organization’s existing security infrastructure and policies.
Step 1: Assess Current Security Posture
A thorough assessment of the current security posture is essential for identifying gaps and prioritizing areas for improvement. This assessment should include:
- Asset Inventory: Identify all critical assets, including data, applications, and infrastructure.
- Vulnerability Assessment: Identify vulnerabilities in existing systems and applications.
- Threat Assessment: Identify potential threats and attack vectors.
Once the assessment is complete, the next step is to develop a Zero Trust implementation plan. This plan should outline the specific steps that the organization will take to implement Zero Trust, as well as the timeline and resources required.

The implementation plan should also include a strategy for communicating the benefits of Zero Trust to stakeholders and obtaining their buy-in.
In conclusion, implementing Zero Trust Architecture requires a step-by-step approach that includes assessing the current security posture, developing a Zero Trust implementation plan, and implementing the plan in a phased manner. By following this approach, organizations can successfully adopt Zero Trust and improve their overall security posture.
Tools and Technologies for Zero Trust Implementation
Implementing Zero Trust Architecture requires a variety of tools and technologies. These tools and technologies can help organizations automate key processes, enforce security policies, and monitor access.
One of the most important tools for Zero Trust implementation is an identity management system. Identity management systems are used to authenticate and authorize users and devices, ensuring that only authorized individuals have access to resources.
Importance of Identity Management Systems
Identity management systems are the foundation of Zero Trust Architecture. They provide the ability to:
- Verify User Identity: Ensure that users are who they claim to be through multi-factor authentication and other methods.
- Manage Access Control: Grant users only the minimum level of access required to perform their duties.
- Monitor User Activity: Track user activity to detect and respond to suspicious behavior.
Other important tools for Zero Trust implementation include network segmentation tools, data encryption tools, and security information and event management (SIEM) systems.
In summary, implementing Zero Trust Architecture requires a variety of tools and technologies. These tools and technologies can help organizations automate key processes, enforce security policies, and monitor access.
Challenges and Considerations for Zero Trust Adoption
Adopting Zero Trust Architecture is not without its challenges. Organizations must carefully consider these challenges and develop strategies to overcome them in order to successfully implement Zero Trust.
One of the biggest challenges is the complexity of implementing Zero Trust across large and complex organizations. Zero Trust requires significant changes to existing security infrastructure and policies, which can be difficult to implement in a phased manner.
Complexity of Implementation
The complexity of implementing Zero Trust can be daunting, but it is essential to approach the process in a structured and methodical way. Key considerations include:
Another challenge is the need for continuous monitoring and validation. Zero Trust requires organizations to continuously monitor and validate access, which can be resource-intensive.
In conclusion, adopting Zero Trust Architecture is not without its challenges. Organizations must carefully consider these challenges and develop strategies to overcome them in order to successfully implement Zero Trust.
| Key Point | Brief Description |
|---|---|
| 🛡️ Zero Trust Principles | Verify explicitly, least privilege access, assume breach, and microsegmentation. |
| 🚀 Automation | Utilize automation tools to streamline Zero Trust implementation and management. |
| 🔑 Identity Management | Implement robust identity management systems for authentication and authorization. |
| 📊 Continuous Monitoring | Continuously monitor and validate access to detect and respond to threats. |
FAQ
▼
Zero Trust Architecture is a security model that assumes no user or device is trusted by default, requiring verification for every access request, regardless of network location. It focuses on protecting resources rather than network perimeters.
▼
CISA is updating its guidance to incorporate lessons learned from real-world implementations, address emerging threats, and provide a clearer, more actionable framework for federal agencies to adopt Zero Trust principles effectively.
▼
The main principles include verifying explicitly, using least privilege access, assuming breach, and employing microsegmentation. These principles ensure continuous validation and minimize the impact of potential breaches.
▼
Organizations can implement Zero Trust by assessing their current security posture, developing a Zero Trust implementation plan, using tools and technologies like identity management systems, and continuously monitoring and validating access.
▼
Challenges include the complexity of implementing Zero Trust across large organizations, the need for continuous monitoring and validation, and the requirement for significant changes to existing security infrastructure and policies.
Conclusion
The updated guidance from CISA on **Zero Trust Architecture** represents a crucial step forward in enhancing cybersecurity for federal agencies. By understanding the core principles, addressing implementation challenges, and leveraging the right tools, organizations can significantly strengthen their defenses against today’s evolving cyber threats. Continuous adaptation and vigilance are key to maintaining a robust Zero Trust posture.




